What is Zero Trust? Zero Trust is a network security strategy based on the philosophy that no person or device inside or outside of an organization’s network should be granted access to connect to IT systems or workloads unless it is explicitly deemed necessary. In short, it means zero implicit trust.
Continue ➤ 11 Anonymous, Secure And Encrypted Private Email Service Providers
What is the difference between VPN and Zero Trust Network? VPNs route traffic through multiple servers and then through a central point in the corporate data center, which can cause latency in the connection. ZTNA solutions, however, connect users to applications directly without having to transmit data through that central point, which reduces latency.
While VPNs have historically had a place in most network security plans, zero trust is a relatively new concept that aims to fill in the security gaps traditional security approaches miss. Thus, when it comes to SSL VPN vs Zero Trust— Zero Trust Security wins with a competitive edge to ensure secure remote access, internal network security, high simplicity, and quality user experience. ZTNA offers better security, more granular control, increased visibility, and a transparent user experience compared to traditional remote access VPN.
1. Cloudflare Zero Trust
Stronger security and consistent experiences for your remote and office users alike. Cloudflare delivers Internet-native Zero Trust services through one unified, composable platform. Secure any user accessing any application, on any device, in any location.
Ensure all traffic in and out of your business is verified and authorized. Check dynamic context to “never trust and always verify” every request. Zero Trust Network Access (ZTNA) enforces default-deny, Zero Trust rules for users accessing all your applications, faster and safer than a VPN.
2. Twingate
Twingate makes it easy to adopt and maintain a Zero Trust networking model. Just map your network, assign access, and connect. Securely connect to your private network on any device with their easy-to-use apps. Twingate feels like magic because it quietly runs in the background and just works.
Twingate was designed from the beginning with a thoughtful approach to security in mind. A key feature of Twingate’s design is that no single component can independently make a decision to allow traffic to flow to another component or Resource in your Remote networks.
3. Sophos ZTNA
Sophos Zero Trust Network Access eliminates vulnerable VPN clients, integrates device health, and removes the implicit trust and broad network access that VPN provides. It allows granular access to resources defined by policies based on health and identity to enhance your security posture.
- Enable Remote Workers – Replace remote access VPN with a superior solution for secure access to the applications and data your remote users need. Remote Access VPN has served us well, but was never designed for this new world. ZTNA provides a much better alternative for remote access by providing better security and threat protection, an easier more scalable management experience, and a more transparent frictionless experience for end-users.
- Micro-Segment Your Applications – Micro-segmentation removes implicit trust and ensures your applications are secure from lateral movement. With VPN, you’re providing network access. With Sophos ZTNA you’re only providing specific application access. Your applications, users and devices are micro-segmented and with the integration of device health into access policies, and continuous authentication verification, you get much better security. This eliminates all the of implicit trust and the lateral movement that comes along with VPN.
- Gate Access – Utilize ZTNA and Microsoft Azure Active Directory to provide secure access control to SaaS Applications like Salesforce and Dropbox. As an alternative or supplement to SaaS application allowed IP ranges, you can utilize ZTNA and your Azure AD identity provider to control access to important SaaS applications – blocking denied devices and unauthorized users from accessing important cloud apps and data.
- Stop Ransomware and Other Threats – Eliminate common attack vectors to keep ransomware and other threats from getting a foothold on your network. Hackers and attackers are leveraging poorly secured remote systems and VPN vulnerabilities to get a foothold on networks to deploy ransomware. Sophos ZTNA helps reduce the surface area and risk of a Ransomware attack by removing a new and growing vector. With ZTNA remote systems are no longer connected “to the network” and only have specific application access.
- Onboard New Apps and Users Quickly – Stand up new applications quickly and securely, easily enroll or decommission users and devices, and get insights into application status and usage. Sophos ZTNA is much leaner, cleaner, and therefore easier to deploy and manage than traditional remote access VPN. It enables better security and more agility in quickly changing environments with users coming and going – making day-to-day administration a quick and painless task and not a full-time job.
- Secure RDP Access – Lockdown and secure RDP access, including new passwordless options using Windows Hello for Business.
4. NordLayer
The protection and security of their client’s remote workforces and business data is fundamental to everything they do at NordLayer. Their information security management systems are certified according to ISO 27001 and support powerful AES-256 military-grade encryption. Their information security policies and procedures follow the SOC 2 Type I compliance requirements. As part of Nord Security, it’s in their DNA to ensure compliance and data security best practices are in place at all times.
- AES 256-bit encryption – NordLayer utilizes military-grade tunnel encryption to hide your traffic and online activity from users on the open internet
- NordLynx (WireGuard) – NordLynx, a WireGuard® based protocol – will allow you to experience WireGuard’s performance benefits without compromising your privacy
- Dedicated IP / Fixed IP – Set up virtual locations for your organization, and prevent unauthorized data access
- Smart Remote Access – Share files endpoint-to-endpoint when multiple user devices are connected to NordLayer
- 2FA – Provide an additional layer of protection on your device by setting up multi-factor authentication to log in to NordLayer
- Centralized settings – Centrally implement and enforce the use of certain NordLayer security policies to your entire organization, including biometric and multi-factor authentication.
- Activity monitoring – Via a central management Control Panel, you can view which users and devices are accessing specific gateways and resources, providing auditable visibility and control of access and activity
5. Perimeter 81
At Perimeter 81, their mission is to simplify secure network, cloud and application access for the modern and mobile workforce. To do so, they are transforming traditional network security technology with one unified Zero Trust Network as a Service. They adhere to the highest standards of software security compliance, so you can rest assured that your organization’s data remains fully protected, they are Certified SOC 2 Type 2, GDPR, CCPA and ISO 27001 Compliant. Reduce your network’s attack surface with Zero Trust Network Access.
- Easily Build, Manage, and Monitor Your Network – Say goodbye to hours of setup and manual configuration. Fully monitor and secure your organization’s most valuable resources from a single dashboard.
- Encrypted – Support for multiple major encryption protocols including IPSec, OpenVPN and WireGuard.
- Lightning-Fast Deployment – In just a few clicks, purchase, provision, and enable secure zero-trust access on-prem, in the cloud, or anywhere in between.
6. Palo Alto Networks
Palo Alto Networks’ Zero Trust is a security model that assumes that all devices and users, including those already inside a network, are untrusted until proven otherwise. It seeks to reduce the risk of cyber attacks by implementing strict access controls and continually verifying the identity and security posture of all devices and users trying to access network resources. Zero Trust helps organizations implement a “never trust, always verify” approach to security, providing a comprehensive approach to securing networks and data against cyber threats.
7. Absolute ZTNA
Absolute ZTNA (Zero Trust Network Access) is a security solution that helps organizations implement a Zero Trust security model. It provides secure access to network resources and applications based on continuous risk assessment and verification of device identity and security posture. Absolute ZTNA allows organizations to restrict access to sensitive data and applications to only trusted devices and users, reducing the risk of cyber attacks. This solution integrates with existing security infrastructure and provides real-time visibility into device and user behavior, enabling organizations to quickly detect and respond to security threats.
8. AppGate SDP
AppGate SDP (Software-Defined Perimeter) is a security solution that provides a secure and scalable way to access network resources and applications. It implements a Zero Trust security model, where access to network resources is granted only after continuous identity and security posture verification of the device and user. With AppGate SDP, organizations can securely connect users to applications and data from any device, anywhere, without the need for a VPN. The solution integrates with existing security infrastructure and provides end-to-end encryption, multi-factor authentication, and continuous monitoring to ensure the security of network access.
9. Illumio ZTS
Illumio delivers a foundational component of any Zero Trust architecture – Zero Trust Segmentation. Unlike prevention and detection technologies, ZTS contains the spread of breaches and ransomware across the hybrid attack surface by continually visualizing how workloads and devices are communicating, creating granular policies that only allow wanted and necessary communication, and automatically isolating breaches by restricting lateral movement proactively or during an active attack. ZTS is a foundational and strategic pillar of any Zero Trust architecture.
- ZTS helps organizations ring-fence and protect high-value applications and data by restricting access to only that which is critical and necessary.
- ZTS helps organizations migrate to the cloud by visualizing hybrid and multi-cloud application workload communications that highlight major security gaps across dispersed architectures.
- ZTS provides complete visibility of assets and traffic flows to overcome incomplete or fragmented visibility into risk.
- ZTS is used to create boundaries between IT and OT systems to stop the spread of OT attacks that easily come in from IT.
- ZTS is used in incident response to defend against active ransomware attacks in minutes.
- ZTS automates effective and consistent cloud security enforcement across hybrid and multi-cloud deployments.
10. Ivanti
Ivanti Neurons for Zero Trust Access uses the web to create a secure connection from the device to an application, eliminating bandwidth and data charges through gateways while constantly verifying the user, their device, and applications based on granular constraints.
- Single client – A Single client for managing access solutions. Most vendors have separate clients for VPN, software gateways and access.
- Web-based – Uses the web to create a secure connection from the device to an application eliminating bandwidth and data charges through gateways.
- Granular safety – Constantly verify user, device, and application based on granular constraints.
- Easy implementation – Easier to implement granular access and conditional access policies.
- Resource-saving – Doesn’t require equipment rip and replaces SaaS delivery and named user.
- Data protection – The Control plane never interacts with customer data eliminating data protection risk.
- Cost-saving – No charge for additional gateways or data traffic.
11. CrowdStrike Zero Trust
The CrowdStrike Zero Trust solution secures your enterprise against modern attacks with the world’s largest unified, threat-centric data fabric to stop breaches in real time on any identity, endpoint and workload — wherever they are. Built on a scalable cloud-native architecture, the CrowdStrike Zero Trust solution adheres to the NIST 800-207 standard, and maximizes Zero Trust protection, covering multi-directory identity stores (Microsoft AD, Azure AD), multi-OS endpoints and workloads across your hybrid enterprise. Stop breaches like supply chain attacks, ransomware and malicious code execution in real time.
12. Trustgrid Remote Access
Remote access tools, such as VPNs and legacy remote desktop tools, lack granular access management controls and can be easily exploited via stolen credentials and session hijacking. Extending remote access to 3rd parties or vendors for support can introduce even more risk.
Trustgrid Remote Access provides secure access to on-premise applications. It eliminates the need for legacy remote user solutions by using a simple web interface to grant access across a range of applications and devices.
Trustgrid Remote Access is ideal for remote maintenance and support of on-premise environments when high degrees of security and compliance are required. Leveraging an organization’s identity provider and connected via their agentless access portal, authorized users have private access to applications without accessing the entire network.
What is the difference between a Personal VPN and Business VPN?
It’s important not to confuse a business VPN with a traditional VPN. A traditional VPN serves only two primary purposes; to mask your IP and help keep your identity anonymous, whereas a Business VPN ensures secure transmission of data through end-to-end encryption through a private network. Although both share the same basic concept of keeping your data safe, a Business VPN provides an impenetrable encrypted tunnel between an organization’s resources and systems and the employees accessing them.
Business VPNs allow your company to control access, similar to authorizing or preventing people from entering a building. By adding or removing users when needed, organizations can protect sensitive information and block access to company servers on a person-by-person basis. Employees transition in and out of companies all the time or only require temporary access. If an employee’s device is stolen, access can quickly be blocked, ensuring company data remains secure.
Having said that, can a company VPN track your activity? If you’re connected to a business VPN provided by your employer, they would probably be able to monitor you. Most business VPNs log employees’ activities and do not guarantee anonymity from your employer.
1. TorGuard Business VPN
TorGuard business VPN accounts come with professional account admin features so you can add new users or remove old ones as needed. The account admin can assign specific dedicated VPN IP’s to any user for secure white listing on restricted resources.
With TorGuard VPN, you can rely on military grade 256-AES encryption. They use only the strongest security protocols such as OpenVPN and WireGuard that ensure no data leaves your company. By using a VPN, your network traffic will stay secure no matter the location.
- Unlimited Speeds + Bandwidth
- 3000+ servers in 50+ countries
- Custom server setups available
- Dedicated lines available
- Encrypted Email accounts
- Dedicated user management portal
- 24/7 Dedicated account manager
- Highly secure encryption standards
- Dedicated VPN IP Addresses
- Stealth VPN and Proxy services
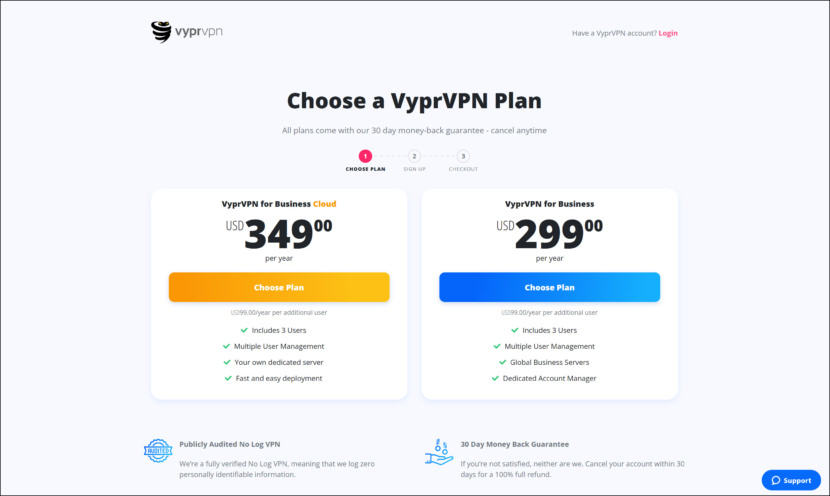
2. VyprVPN for Business
Golden Frog develops software and services that provide reliability, performance and security. We’re dedicated to inventing and perfecting tools that offer a fuller, richer online experience. Encrypt your internet connection with VyprVPN to protect your privacy and secure your connection. Prevent your ISP or third-party snoops from viewing your online communications, location and browsing activity.
Escape government censorship and Internet restrictions. Whether you live in China, Russia, Turkey, or the Middle East, restore your access to a free and open Internet with VyprVPN. Improve your speed, access geo-blocked content and stay secure while streaming online. Achieve the best streaming experience from any location with VyprVPN.
3. PureDome Business VPN
PureDome enables data access control and helps companies divide assets into several organized sets. This ensures that only authorized users can access said company assets. Moreover, the best VPN for freelancers also protects information and ensures that data are encrypted for secure transmission. PureDome’s best enterprise VPN solution integrates with essential network equipment and endpoints.
The IPSec protocol creates a corporate VPN tunnel by negotiating SA (Security Associations) with the IKE (Internet Key Exchange) management protocol to create a secure and verified communication channel between the user, device, and network resources. PureDome takes great pride in its zero logs policy, ensuring companies do not have to worry about the misuse of their private and confidential information.