Category: Computer and Internet Security » WiFi Security
Who hacked my Wifi? Is your home router vulnerable to the NetUSB or Backdoor? Unless you update your router’s firmware, chances are, your home network is exposed to hijacking and hacking. Today’s modern router by TP-Link, D-Link, Asus, NetGear, Cisco Linksys and many more comes with a simple web based update, just visit the router’s web interface (192.168.1.1) and hit the update button.
Related Article 😍💰👉 15 Free Antivirus For Windows 10 – Microsoft Defender Alternatives
As of late, some security companies are releasing their own router with antivirus, they are Bitdefender BOX, BullGuard Dojo and Norton Core just to name a few. These routers are highly recommended for businesses that provide free public wifi.
New software vulnerabilities are being discovered in many smart devices every day, and hackers are taking advantage of these security flaws to target homes and businesses. It is time to start thinking about the security of your smart devices.
1. Avast Wi-Fi Inspector
Router Scanner | Free via Avast Free Antivirus
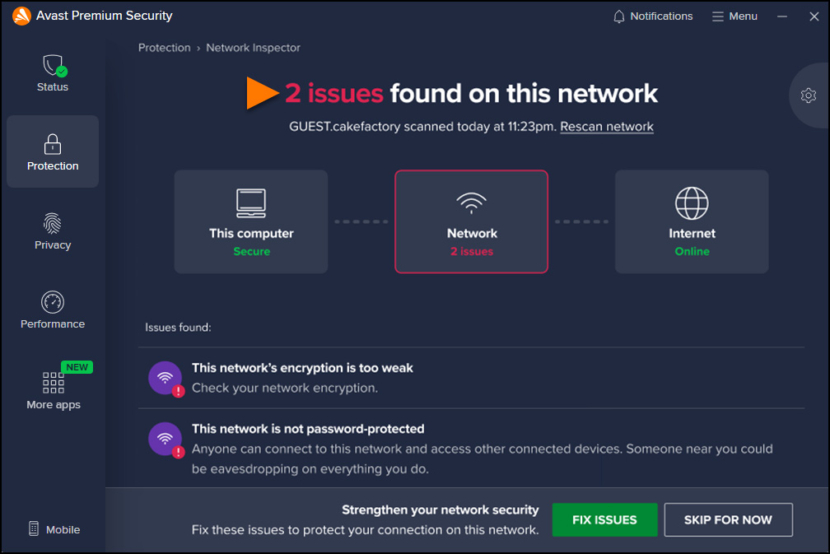
Wi-Fi Inspector scans your network for vulnerabilities and identifies potential security issues that open the door to threats. This feature checks the status of your network, devices connected to the network, and router settings. Wi-Fi Inspector helps you secure your network to prevent attackers from accessing it and misusing your personal data.
Wi-Fi Inspector can be found in Avast Free Antivirus, it scans your network for vulnerabilities and identifies potential security issues that open the door to threats. This feature checks the status of your network, devices connected to the network, and router settings.
Connect more safely, even on unsecured Wi-Fi networks, block hackers and intruders from piggybacking on your network more easily, and help keep them away from your sensitive, personal files. Wi-Fi Inspector helps you secure your network to prevent attackers from accessing it and misusing your personal data. Wi-Fi Inspector exposes the following vulnerabilities:
- Weak or default passwords (for Wi-Fi and router administration)
- Router firmware vulnerabilities (for most common vendors)
- Non-encrypted, unsecured wireless networks
- DNS hijacking (on devices and routers)
- Open network ports (for remote access, Telnet, etc.)
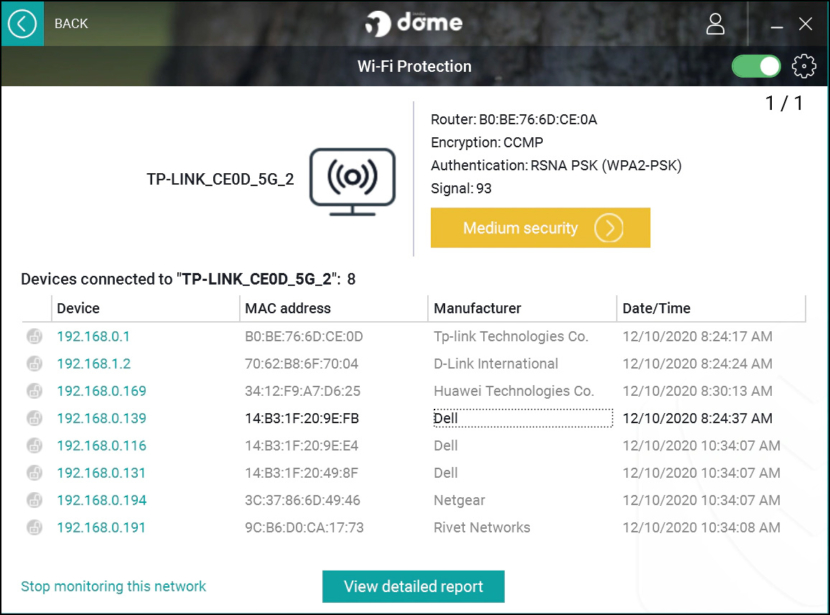
2. Panda Dome Wi-Fi Protection
Router Scanner | 30-Days Trial via Panda Dome, Advanced, and Complete
Panda Protection Service (available in Panda Internet Security) includes a Wi-Fi Monitor that allows users to see the computers connected to their Wi-Fi network, helping users to detect intruders in their WiFi network, audit the security of the network, etc.
The WiFi protection is available from the widget WiFi protection available from the main interface and it offers the following options. WiFi auditing. Audits the Wi-Fi network searching for vulnerabilities, and provides recommendations to improve network security. This analysis checks the following aspects.
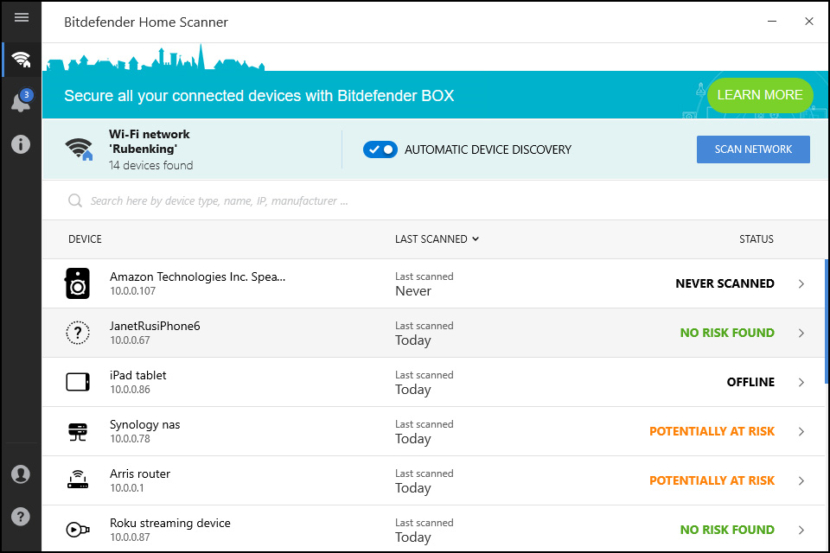
3. Bitdefender Home Scanner
Router Scanner
Free and super-fast Wi-Fi scanner for your home network. Bitdefender Home Scanner looks for vulnerable devices and passwords, and offers detailed security recommendations for your home network. Home Scanner lets you see all devices connected to your home network. You get an alert every time an unknown device connects to your wi-fi. Which means you can instantly boot out freeloaders and prevent connection slowdowns.
Once logged in to your Bitdefender account (a link is provided to create one), it will scan for and ask you to confirm your home network, and you can begin scanning. You are notified when the scan has completed successfully. You are then informed of any issues, and you can go forward to risk or no risks found to find details including last scanned, MAC address, IP address, manufacturer, and device type.
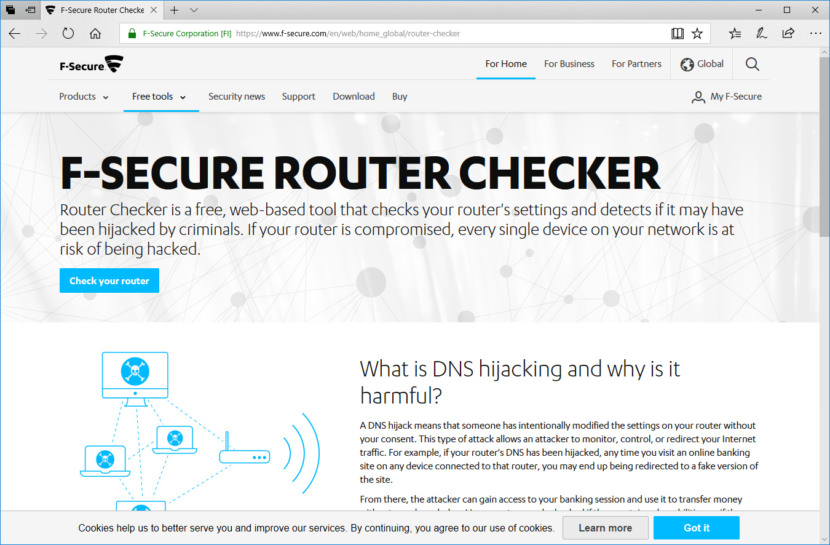
4. F-Secure Router Checker
Router Scanner | Free 30-Days Trial via F-Secure Total
Router Checker is a free web-based tool you can use to check your device’s connection to its DNS resolver, to make sure it is connecting to an authorized DNS server. A mismatch between the two may indicate DNS hijacking is underway.
A DNS hijack means that someone has intentionally modified the settings on your router without your consent. This type of attack allows an attacker to monitor, control, or redirect your Internet traffic. For example, if your router’s DNS has been hijacked, any time you visit an online banking site on any device connected to that router, you may end up being redirected to a fake version of the site.
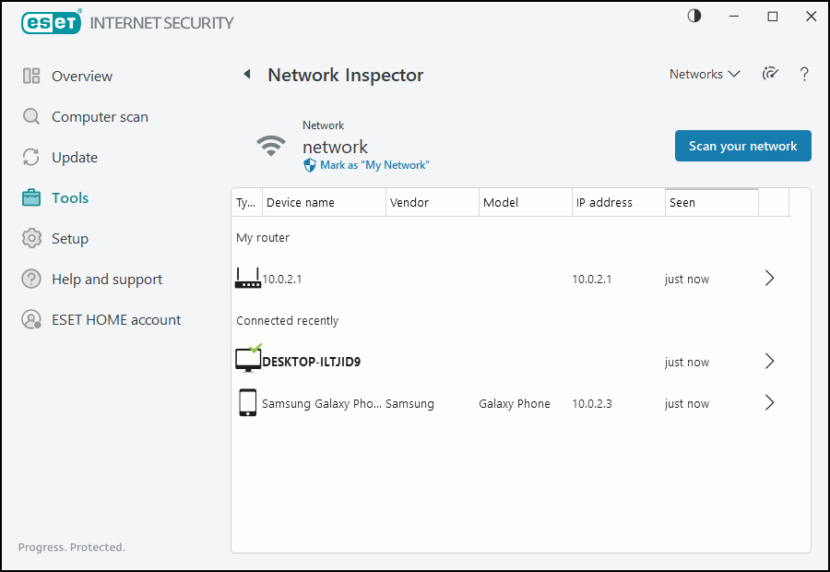
5. ESET Network Inspector
Network Scanner | Free 30-Days Trial via ESET Essential, Premium, and Ultimate
Connected Home Monitor is a new feature included in ESET Smart Security Premium and ESET Internet Security. This feature was introduced as Home Network Protection in version 10. This diagnostic tool provides information about the security of your router. It also displays a list of devices connected to your network.
It may be necessary to consult support resources for your router or contact your internet service provider to resolve certain issues within your home network if you lease or own a device they provided.
Below are several notifications that can be shown when ESET Internet Security detects some vulnerability issue on your router. Each notification contains a short description and provides some solution or steps that should be done to minimize vulnerability risk of your router. If you are not familiar with router changes, we recommend contacting your router manufacturer or internet provider.
- Potential vulnerability found – Your router may contain known vulnerabilities that could make it easy to attack and exploit. Update your router’s firmware.
- Vulnerability found – Your router contains known vulnerabilities that make it easy to attack and exploit. Update your router’s firmware.
- Threat found – Your router is infected by malware. Restart your router and repeat the scan.
- Weak router password – The password on your router is weak and can be easily quessed by someone else. Change the password in your router.
- Malicious network redirection – Your internet traffic appears to be redirected to malicious websites. This can mean your router is compromised. Change the DNS server setting in your router.
- Open network services – Your router runs network services that may be exploited by others. This can be due to poor configuration or a compromised router. Check your router’s configuration.
- Sensitive open network services – Your router runs sensitive network services that may be exploited by others. This can be due to poor configuration or a compromised router. Check your router’s configuration.
- Firmware outdated – The firmware on your router is outdated and may contain vulnerabilities. Update the firmware on your router.
- Malicious router setting – This DNS server that your uses is malicious and may send you to dangerous websites. This can mean your router is compromised. Change the DNS server setting in your router.
- Network services – Your router runs common network services. These are needed by the network and are probably safe. Check your router’s configuration.
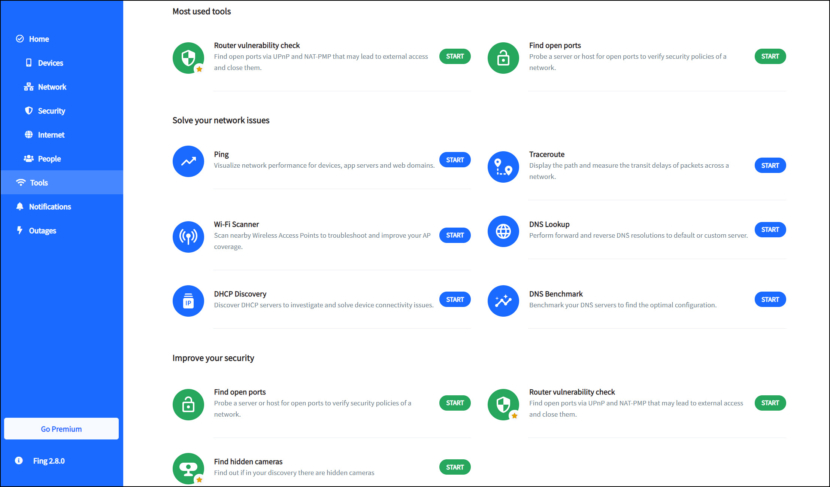
6. Fing
Network Scanner | Freemium with basic features
Fing helps you understand most of your home network. See all the devices connected to your Wi-Fi, run network scanners, monitor your Internet speed, know your security level, set automated vulnerability checks, and much more. Elevate your network’s protection by blocking intruders, detecting unknown devices, and automating router vulnerabilities checks.
- Automate router vulnerability checks – Strengthen your security: monitor potential weaknesses in your network, preventing unauthorized access and ensuring your systems remain safe from exploitation.
- Find hidden cameras on any network you are – Ensure your safety in rental spaces: our database includes more than 12 million cameras, and with our advanced scanning technology you can get peace of mind and a secure stay.
- Block unwanted devices – Fortify your network against unauthorized access: permanently blacklist unwanted devices from connecting, keeping your Wi-Fi safe from repeat intruders.
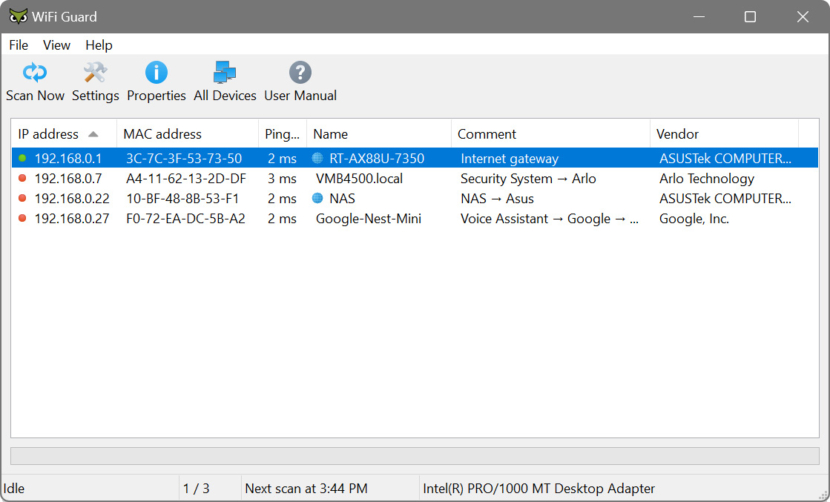
7. SoftPerfect WiFi Guard
Network Scanner
SoftPerfect WiFi Guard is an essential tool for everyone running a small wireless network and striving to keep it secure. Generally, modern Wi-Fi networks are well protected, but there are a number of weaknesses that can compromise your Wi-Fi password; this includes vulnerabilities in encryption and brute force attacks. As a result, someone can gain unauthorised access to your Internet connection and LAN and exploit them while staying unnoticed.
Here comes their little application: it will alert you if your network is used without your knowledge. WiFi Guard is a specialised network scanner that runs through your network at set intervals and reports immediately if it has found any new, unknown or unrecognised connected devices that could possibly belong to an intruder.
Key features
- Pings computers and other network devices and displays those alive.
- Detects firewalled computers that do not respond to ping.
- Scans your network at a specified interval.
- Immediately alerts you if an unknown device is found.
8. Advanced IP Scanner
Network Scanner
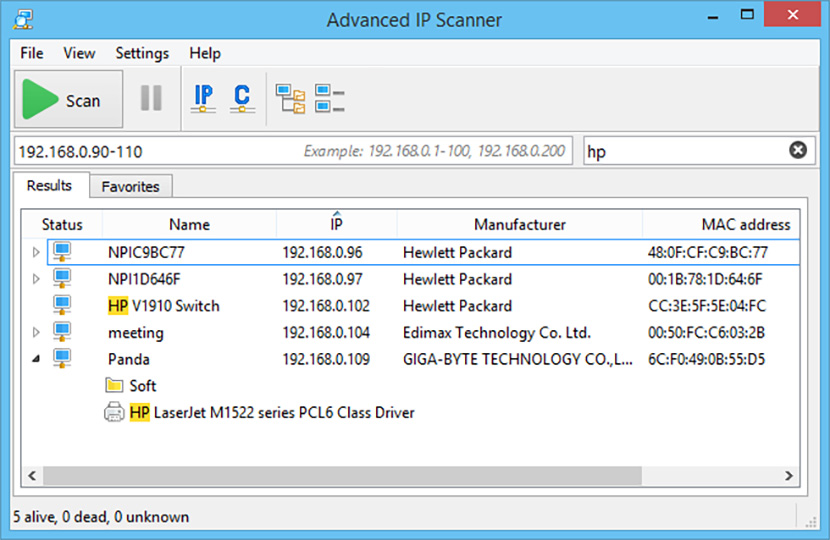
Free and fast network scanner allows you to quickly retrieve information about network devices and get access to their various resources such as shared folders, HTTP, HTTPS, FTP, RDP and Radmin. The program does not require installation and has a simple and user-friendly interface. Advanced IP Scanner is widely used by system administrators and home users for network management and monitoring.
Reliable and free network scanner to analyse LAN. The program shows all network devices, gives you access to shared folders, provides remote control of computers (via RDP and Radmin), and can even remotely switch computers off. It is easy to use and runs as a portable edition. It should be the first choice for every network admin.
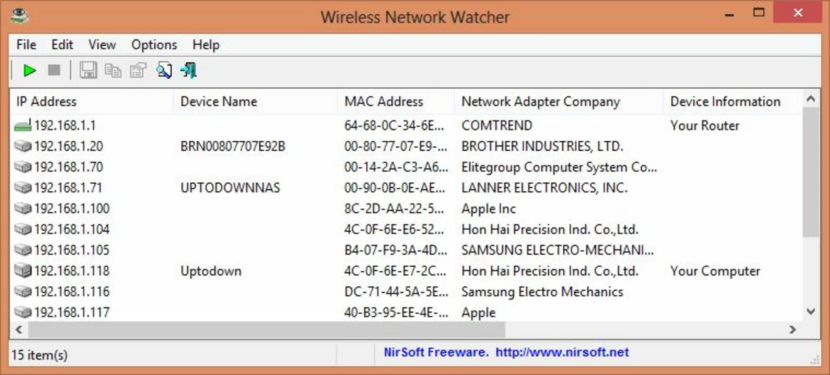
9. Wireless Network Watcher
Network Scanner
Wireless Network Watcher is a small utility that scans your wireless network and displays the list of all computers and devices that are currently connected to your network. For every computer or device that is connected to your network, the following information is displayed: IP address, MAC address, the company that manufactured the network card, and optionally the computer name.
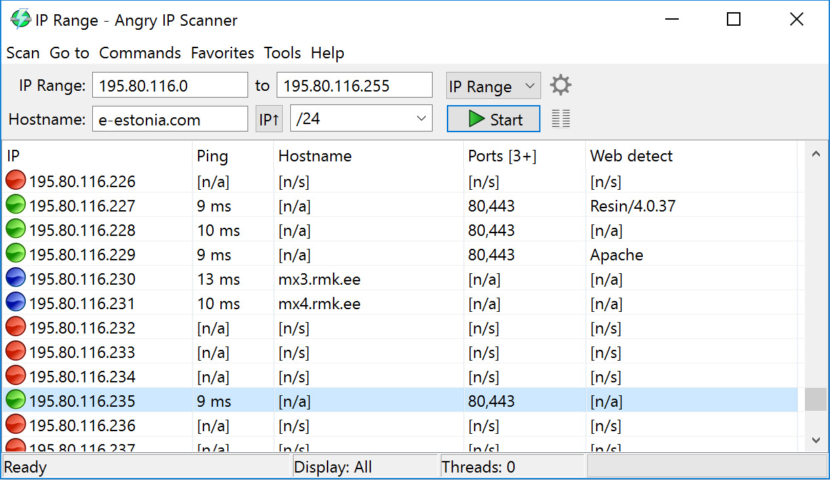
10. Angry IP Scanner
Network Scanner
Angry IP Scanner (or simply ipscan) is an open-source and cross-platform network scanner designed to be fast and simple to use. It scans IP addresses and ports as well as has many other features. It is widely used by network administrators and curious users around the world, including large and small enterprises, banks, and government agencies. It runs on Linux, Windows, and macOS, possibly supporting other platforms as well.
- Scans local networks as well as Internet
- IP Range, Random or file in any format
- Exports results into many formats
- Extensible with many data fetchers
- Provides command-line interface
11. Trend Micro HouseCall
Network Scanner
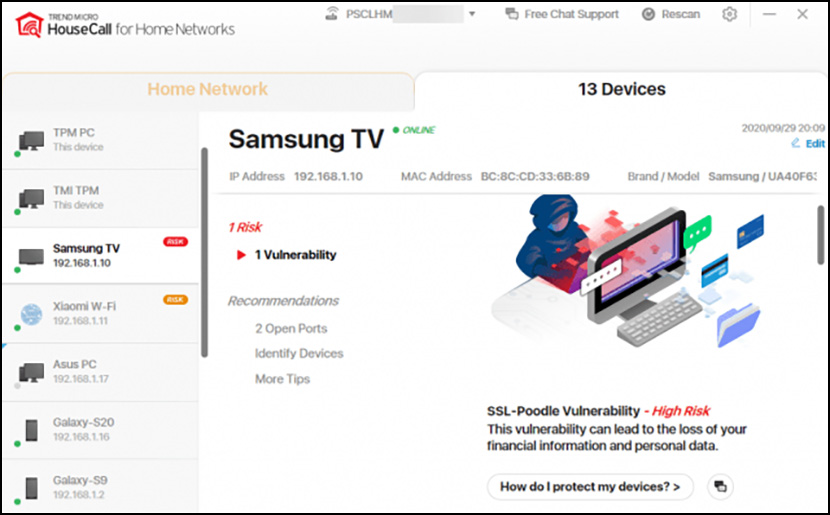
As the number of devices connected to your network continues to grow, so do the opportunities for hackers to cause trouble. HouseCall for Home Networks scans all of your home network devices for vulnerabilities and recommends how to eliminate them. An increasing number of smart devices – like IP cameras, smart televisions, and storage devices – now connect to home networks.
Many devices have security issues that attackers can use to take control of them or the home network itself, which can lead to privacy leaks or much worse. HouseCall for Home Networks scans all of the devices connected to your home network to identify potential risks and offer suggestions about how to eliminate them.
Use a simple one-tap scan to detect all of the devices connected to your home network and check them for security risks. HouseCall for Home Networks also provides helpful advice on protecting your devices and keeping your digital life safe. Trend Micro HouseCall for Home Networks scans your home network to help you answer the following questions:
- Who has connected to my home Wi-Fi network?
- Are my home network and connected devices safe from hackers and malicious software?
- What should I do if my network or devices are vulnerable?
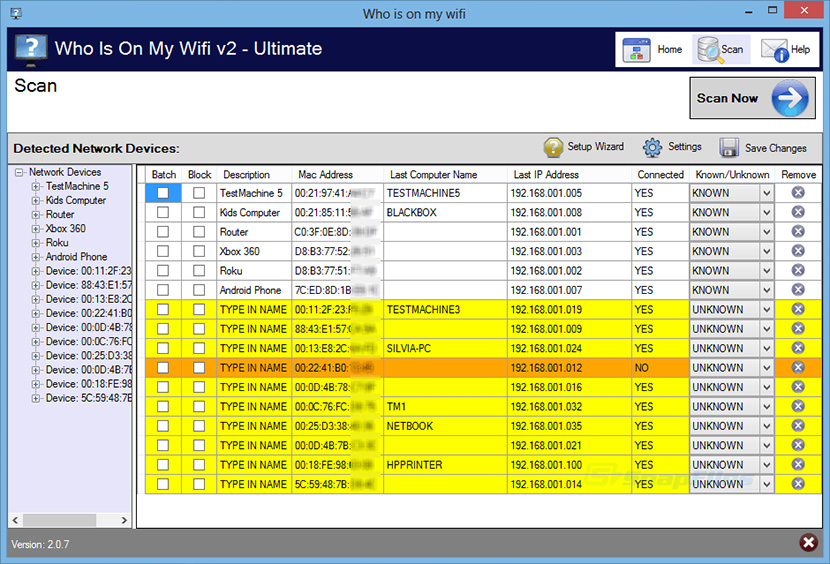
12. Who Is On My WiFi
Network Scanner
[ Discontinued ] Who’s On My Wifi solutions are built to be as easy as possible to detect unknown devices on your home or business network. They focus on building unique solutions for homes and small businesses instead of just stripping down complicated enterprise products. And they work hard everyday to make them easier to use over time.
- Shows all devices on a network overtime.
- Connects with Optional Analytics Subscription.
- Easy to Install on Windows computers.
- Fully Compatible with Analytics Subscription
- Agent per Subnet based detection
- DHCP Server per Scope based detection
- Includes Privacy and Shared Key Features
WEP vs. WPA vs. WPA2 Comparison
How do Wifi wireless get hacked? With the right software such as Air Crack or Backtrack, one can easily break any WEP encryption keys. What AirCrack does is it gathers all the data transmitted between your router and your devices, compiles it and then computes all the possible combinations. With today’s processing power and the weakness in WEP, it takes less than 10 minutes to reveal your WEP security key on a busy network.
Deauthorizing Wireless Clients with Aircrack-ng, the four-way-handshake and WEP vs WPA cracking
WPA has its own weakness too, but it is harder to crack. WPA2 is highly recommended for SME or enterprise; remember than anything man made can be unmade. WPA2 is crackable too, but it will require too much effort and time. It is easier for the hacker to look for someone using WEP instead of wasting time breaking the WPA2 security code. Below is a simple side by side comparison between WEP, WPA and WPA2.
WEP | WPA | WPA2 | |
|---|---|---|---|
| Name | Wired Equivalent Privacy | Wifi Protected Access | Wifi Protected Access 2 |
| Combo | 24 bit initialization keys 16.7 million combination | 48 bit initialization keys 500 trillion combinations | 48 bit initialization keys 500 trillion combinations Advanced Encryption Standard |
| Encryption | 64 bits 128 bits | 64 bits 128 bits | 64 bits 128 bits |
| Keys | Static encryption keys | Unique encryption key | Unique encryption key |
| Speed | Not much processing power | Somewhat processing power | Requires greater processing power |
| Master Key | Master keys are used directly | Master keys are never directly used | Master keys are never directly used |






It is a very helpful assessment of home security inspection tools.
what security issues
security or performance issues are found
Just checked and F-Secure Router Checker appears to now be a subscription service.