Category: The Web » Wordpress, Themes and Plugin
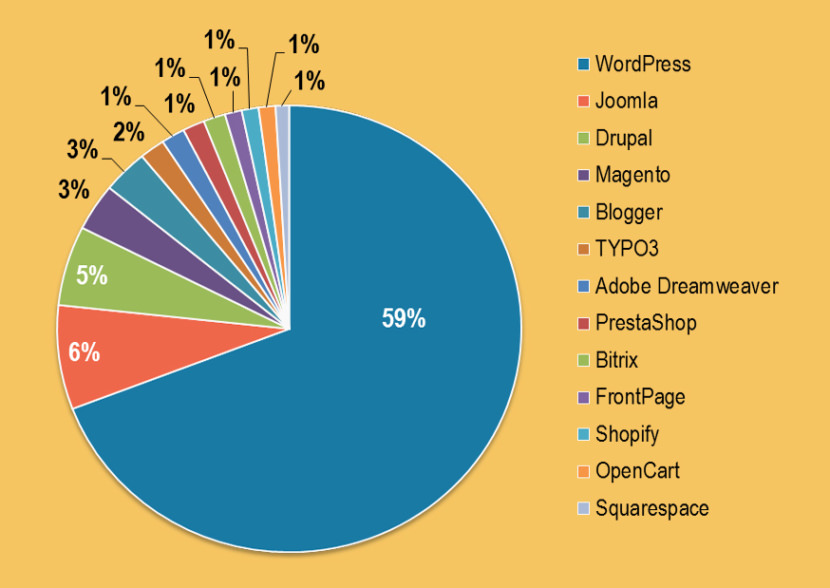
According to W3Techs, WordPress is used by 58.9% of all the websites powered by the top 5 content management system (CMS), these CMS are Drupal, Joomla, Magento and Blogger. As for the entire website on the internet, WordPress powers approximately 27.8% of all websites, the percentage of websites using WordPress is on the rise and continues to grow.
Related Article 😍💰👉 5 Free Linux OS For Penetration Testing, IT Security Assessments And Network Vulnerabilities
This is why WordPress is the favorite target by hackers, if you run WordPress with lots of plugins for your enterprise clients, it is even more important to test the site for all vulnerabilities, especially if it is used for eCommerce via the WooCommerce plugin. These free Web Penetration Tools will perform all sort of vulnerability test on your WordPress site, this is important because more often than not, outdated plugins and themes are one of the leading causes for security breaches.
The WordPress official site has a list of things to do to harden your WordPress. If you are using a Dedicated Server or Virtual Private Server with root access to the OS, consider installing ModSecurity, it is an Open Source Web Application Firewall. Fail2ban on the other hand is a BruteForce stopper by blocking IP addresses that tries to guess your login user ID and Password for more than 5 times.
Based on my experience, hackers love to inject a redirect code into .htaccess, they will attempt to redirect traffic from Google to a different page they created within your site, usually these sites are designed to steal credit card and banking information. The other way around this is to disable .htaccess and have the code coded into the OS.
This is a better solution and the best part is, it makes your apache server run faster, which means an even faster website. Do consider installing and subscribing to these auditing, malware scanner and security hardening services:
1. OWASP Zed Attack Proxy Project
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications. It’s also a great tool for experienced pentesters to use for manual security testing.
- Intercepting Proxy
- Traditional and AJAX spiders
- Automated and passive scanner
- Forced browsing
- Fuzzer
- Dynamic SSL certificates
- Smartcard and Client Digital Certificates support
- Web sockets support
- Plug-n-Hack support
- Authentication and session support
2. Burp Suite Free Edition
Burp Suite is the leading software for web security testing. Thousands of organizations use Burp Suite to find security exposures before it’s too late. Coverage of over 100 generic vulnerabilities, such as SQL injection and cross-site scripting (XSS), with great performance against all vulnerabilities in the OWASP top 10. Burp Scanner is designed by industry-leading penetration testers. Its advanced feedback-driven scanning logic is designed to reproduce the actions of a skilled human tester.
- Automated crawl and scan – Support for numerous types of attack insertion points within requests, including parameters, cookies, HTTP headers, parameter names, and the URL file path.
- Advanced scanning for manual testers – Use the passive scanning mode to identify flaws such as information disclosure, insecure use of SSL, and cross-domain exposure.
3. Codename SCNR (Arachni Scanner)
Arachni is a feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of modern web applications. It is free, with its source code public and available for review.
It is multi-platform, supporting all major operating systems (MS Windows, macOS and Linux) and distributed via portable packages which allow for instant deployment. Out of the box, Arachni has all the full featured support and vulnerability analysis that one would expect from a first class web application scanner. All the usual suspects are supported, including:
- XSS (with DOM variants)
- SQL injection
- NoSQL injection
- Code injection
- File inclusion variants
In addition, Arachni’s analysis techniques are unparalleled in reliability, accuracy and resiliency, even under unstable network conditions or when dealing with misbehaving web applications.