Category: Computer and Internet Security » VPN & ZTN
How to anonymize your footprint online without being tracked by the NSA, FBI, CIA and government? It is a well known ‘secret’ that all governments spy on their own citizens. Is it good or bad? It depends, there are always 2 sides to a coin, for instance.
Related Article 😍💰👉 2 Browser Addon to Auto Bypass Internet Censorship
- Government uses the internet to track down pedophile, which is good.
- Government uses the communication network to hunt down and stop terrorist from planting bombs, which is good.
- Government uses the net to spy on foreign government (North Korea for example), to better protect us from foreign missile threat, which is a must.

The problem arises when it is abused by the current government to stay in power – forever. This includes tracking and blackmailing journalists that expose certain leaders. This can be seen in Russia, China, Iran, Saudi Arabia and more, where there is Freedom of Speech, but no Freedom after Speech. Surf anonymously and send secure encrypted email with these three free services. Big brother is watching.
1. Tor Project Anonymiser
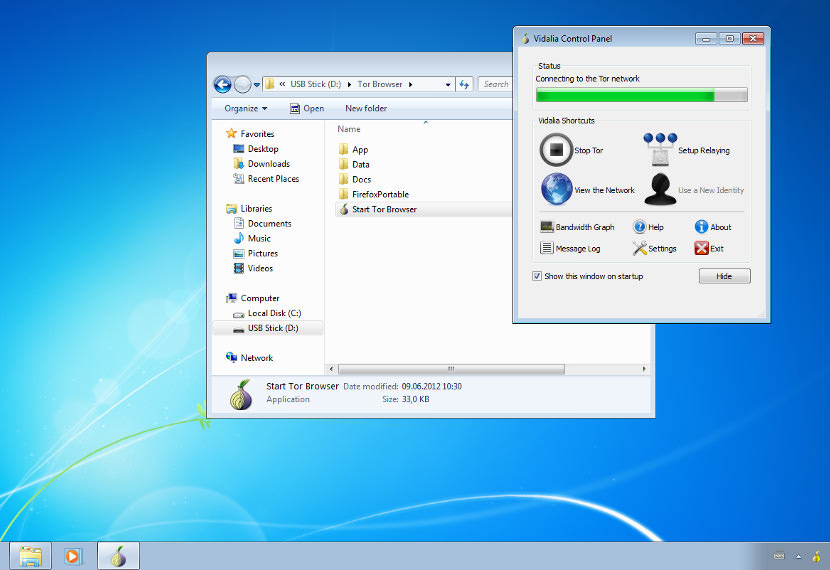
Tor is a free encryption software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security. Protect your privacy. Defend yourself against network surveillance and traffic analysis. Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location. Tor works with many of your existing applications, including web browsers, instant messaging clients, remote login, and other applications based on the TCP protocol.
- Tor Web Browser / Onion Server Routing – Tor Browser contains everything you need to safely browse the Internet with anonymous email.
- Orbot App – Tor for Google Android devices.
- Tails OS – Live CD/USB operating system preconfigured to use Tor safely.
Surf Anonymously and Hide IP Address with Tor Browser. Tor Browser is perhaps the easiest way to surf the internet without revealing your IP address or identity. Based on my experience, Tor Browser is slow but if you are more concerned about privacy, this is a good trade off.
As shown in the video below, Jacob Appelbaum introduces the Tor Project and the Tor Network – an anonymity network used to protect people online. It is used by many people around the world to circumvent censorship and to stay safe online.
2. Freegate
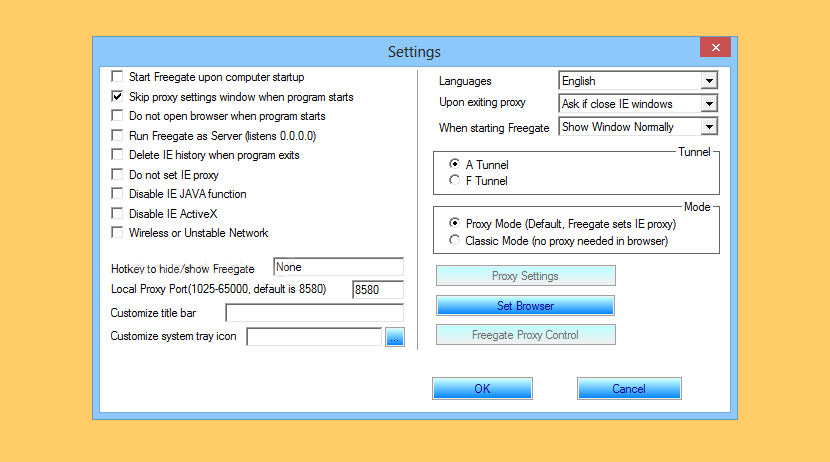
Freegate is an anti-censorship software for secure and fast Internet access. It was developed and maintained by Dynamic Internet Technology Inc. (DIT), a pioneer in censorship-circumvention operations. Freegate works by tapping into an anti-censorship backbone, DynaWeb, DIT’s P2P-like proxy network system. Freegate’s anti-censorship capability is further enhanced by a new, unique encryption and compression algorithm in the versions of 6.33 and above.
- users access web sites overseas as fast as their local ones;
- requires no installation or change in system setting;
- a single executable file on a Windows platform.
3. Invisible Internet Project (I2P)
I2P is an anonymous overlay network – a network within a network. It is intended to protect communication from dragnet surveillance and monitoring by third parties such as ISPs. To anonymize the messages sent, each client application has their I2P “router” build a few inbound and outbound “tunnels” – a sequence of peers that pass messages in one direction (to and from the client, respectively).
In turn, when a client wants to send a message to another client, the client passes that message out one of their outbound tunnels targeting one of the other client’s inbound tunnels, eventually reaching the destination. Every participant in the network chooses the length of these tunnels, and in doing so, makes a tradeoff between anonymity, latency, and throughput according to their own needs. The result is that the number of peers relaying each end to end message is the absolute minimum necessary to meet both the sender’s and the receiver’s threat model.
4. DuckDuckGo
DuckDuckGo is a search engine hosted around the world that provides you with anonymous search results compiled from “about 50” sources, including Yahoo! Search BOSS; Wikipedia; Wolfram Alpha; Bing; its own Web crawler, the DuckDuckBot; and others. It also uses data from crowdsourced sites, including Wikipedia, to populate “Zero-click Info” boxes – grey boxes above the results that display topic summaries and related topics. They don’t store your personal info, search, and history. Anonymous, unlogged web searches.
5. JonDo the IP changer
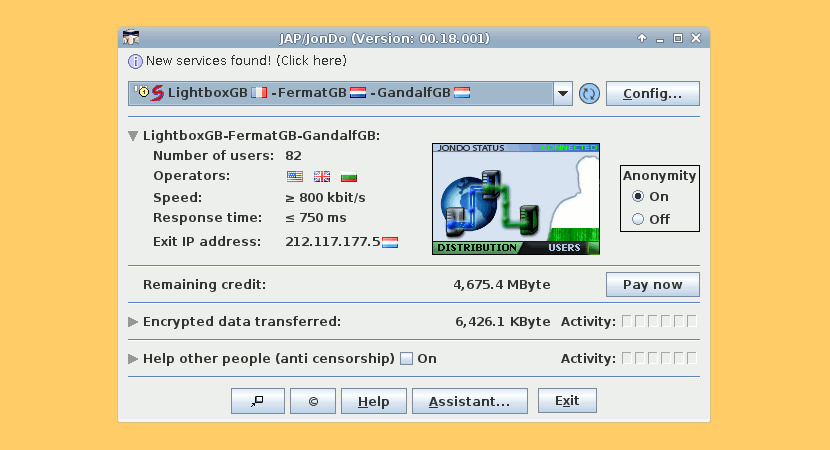
You may use JonDonym for anonymous surfing, anonymous email, chats and other purposes. JonDo, formerly JAP, is the ip changer proxy tool you have to install on your computer. It acts as a proxy and will forward the traffic of your internet applications multiple encrypted to the mix cascades and so it will hide your ip address. It is a Java application, open source and you can download it for free. You may use JonDonym for free, but free mix cascades are restricted in some cases. Full speed and anonymisation features you will get only with a premium account.
JonDo will provide an anonymisation proxy for you, but it does NOT change your system setting. You have to configure the proxy setting of each internet application you want to use anonymous with JonDonym by self.
6. Tails
Tails is a live system Operating System that aims to preserve your privacy and anonymity. It helps you to use the Internet anonymously and circumvent censorship almost anywhere you go and on any computer but leaving no trace unless you ask it explicitly.
It is a complete operating system designed to be used from a DVD, USB stick, or SD card independently of the computer’s original operating system. It is Free Software and based on Debian GNU/Linux. Tails is a live operating system that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity, and helps you to:
- use the Internet anonymously and circumvent censorship;
- all connections to the Internet are forced to go through the Tor network;
- leave no trace on the computer you are using unless you ask it explicitly;
- use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging.
The Silent Order NSA Sees Everything Hears Everything Documentary
Since its inception in 1952, the National Security Agency has been shrouded in secrecy; for years the White House denied its very existence. For the first time since 9/11 changed everything, cameras go beyond the closed doors of the NSA, deep inside the agency’s over 2 million square foot top-secret compound.
Intelligence organization of the United States government, responsible for global monitoring, collection, and processing of information and data for foreign intelligence and counterintelligence purposes – a discipline known as signals intelligence (SIGINT). NSA is concurrently charged with protection of U.S. government communications and information systems against penetration and network warfare. Although many of NSA’s programs rely on “passive” electronic collection, the agency is authorized to accomplish its mission through active clandestine means, among which are physically bugging electronic systems and allegedly engaging in sabotage through subversive software.
Moreover, NSA maintains physical presence in a large number of countries across the globe, where its Special Collection Service (SCS) inserts eavesdropping devices in difficult-to-reach places. SCS collection tactics allegedly encompass “close surveillance, burglary, wiretapping, breaking and entering”.
Unlike the Defense Intelligence Agency (DIA) and the Central Intelligence Agency (CIA), both of which specialize primarily in foreign human espionage, NSA does not unilaterally conduct human-source intelligence gathering, despite often being portrayed so in popular culture. Instead, NSA is entrusted with assistance to and coordination of SIGINT elements at other government organizations, which are prevented by law from engaging in such activities without the approval of the NSA via the Defense Secretary.
As part of these streamlining responsibilities, the agency has a co-located organization called the Central Security Service (CSS), which was created to facilitate cooperation between NSA and other U.S. military cryptanalysis components. Additionally, the NSA Director simultaneously serves as the Commander of the United States Cyber Command and as Chief of the Central Security Service.





While there are many types of proxies out there, your article mentions Web Proxies in the title and VPN in the body.
Typically I avoid web proxies because they are not secure. This is one exception to that and it’s a combination web proxy and VPN, that MegaProxy. I tried them and was impressed by how it worked. It creates an SSH tunnel so you get the best of both worlds, a web proxy and a secure proxy.
Overall though I like true VPN or software based proxies like the ones you mentioned in the post. Some of the open source stuff can be hard to use, but it certainly does the job.
how to hide your IP address and protect your privacy?
send to me the new proxy sites
send to me the new proxy sites
send to me the new proxy sites
A Free and fast to use internet web proxy server, no more blocked websites just use our anonymous free web proxy internet server.
You want an anonymous or high anonymous proxy server?
A web proxy server is a server that you can use to take the place of another server and act as that server in every way. While the proxy server will still be getting everything it needs from the normal server, you will not interact with the normal server in any way and in fact this means that the proxy web server will act as a middle man of sorts between you and the server that you wish to interact with.I have a tried a hardware also which is wonderful little tool helping me to browse anonymously.
which offers secure free anonymous web proxy surfing?
hi. please send tome new proxy server tanks.
Surfing the Internet service with our public webproxy server makes your browsing … Browse anonymously and bypass your school, college or workplace network
I downloaded I2P and install successfully but i couldn’t set up and run this software. I set proxy as the guide but my laptop couldn’t connect internet.
Are there any videos guide to run this software step by step ? I searched on Youtube but they all run on Linux or Ubuntu not windows